Console error after upgrade to 2.1.0
-
@phenomlab said in Console error after upgrade to 2.1.0:
For a proof of concept, I completely stripped all plugins, removed the custom JS, Custom CSS, and Custom Header.
Upgraded to 2.1.0 and STILL get the same error message in the ACP console@baris see this thread
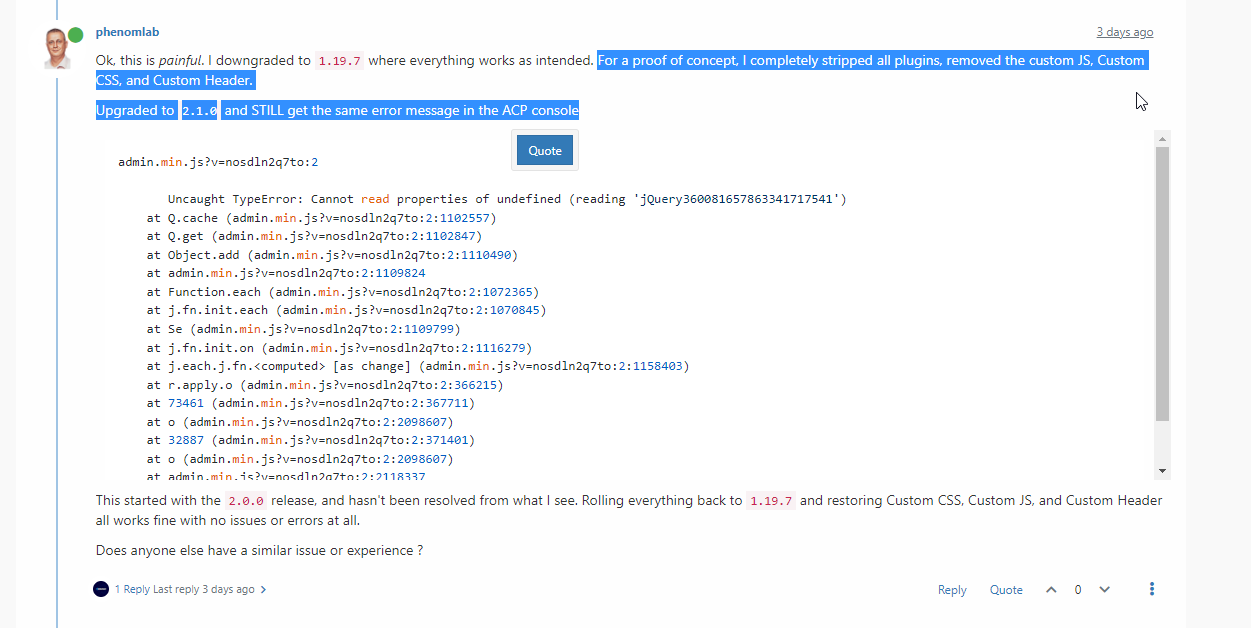
-
What browser are you using? Have you tried other browsers?
-
@phenomlab https://sudonix.dev is your your dev site right? I created an account there, if you give me admin access I can take a look. Maybe I can spot something that is different from this site.
-
@baris yes, that's my dev site. The issue with giving you admin rights is that I can't access anything in the ACP to do so ! The only way this would work is for me to downgrade the forum, grant you admin, then upgrade again - unless there's a way to do this from the database ?
Edit - ok, done from frontend via groups. Good to go.
-
@phenomlab The issue was with the customize plugin, I disabled it on your forum and the error is gone. I will publish a new version of that once I get access to it. For anyone wondering this is the fix https://github.com/NodeBB/nodebb-plugin-customize/commit/e90dcb9be7c8c3b43715d4dc3310c045615a9998
-
@baris thanks for this. I can confirm this is now working, but what's really odd here is that previously, the error persisted even with all plugins disabled.
I'm curious to understand if the two plugins I previously referenced that received updates in between me reporting this issue were perhaps part of the issue as with all plugins disabled, the issue persisted. Even clearing all caches did nothing.
Very odd indeed, but thanks for finding the culprit. I've upgraded this plugin, and now everything is working.
