This is a good time to make sure that everyone in your broader community is using Signal and knows how to anonymize their identity on it.
-
This is a good time to make sure that everyone in your broader community is using Signal and knows how to anonymize their identity on it. This flier offers QR codes to make it easy. You can print out this design here:
https://cdn.crimethinc.com/assets/articles/2024/11/09/signal.pdf
You could use the blank space on the flier to add a third QR code directing people to a local announcements-only Signal thread to stay abreast of developments.
You can learn how to set one up here:

The Sunbird: How to Start an Announcements-Only Thread on Signal
Organizers describe how they established an announcements-only Signal thread for the Palestine solidarity movement to share news and coordinate.
CrimethInc. (crimethinc.com)

-
Nazi trumps fuck off.replied to CrimethInc. Ex-Workers last edited by
Relaying this from people smarter than me about these things: It's a bad idea to normalize scanning QR codes on random flyers. At minimum, have the URL printed out so people can manually type it in.
-
Nazi trumps fuck off.replied to Nazi trumps fuck off. last edited by
A couple examples of why you shouldn't scan random QR codes: https://www.techradar.com/computing/cybercrime/quishing-is-the-qr-code-scam-you-need-to-watch-out-for
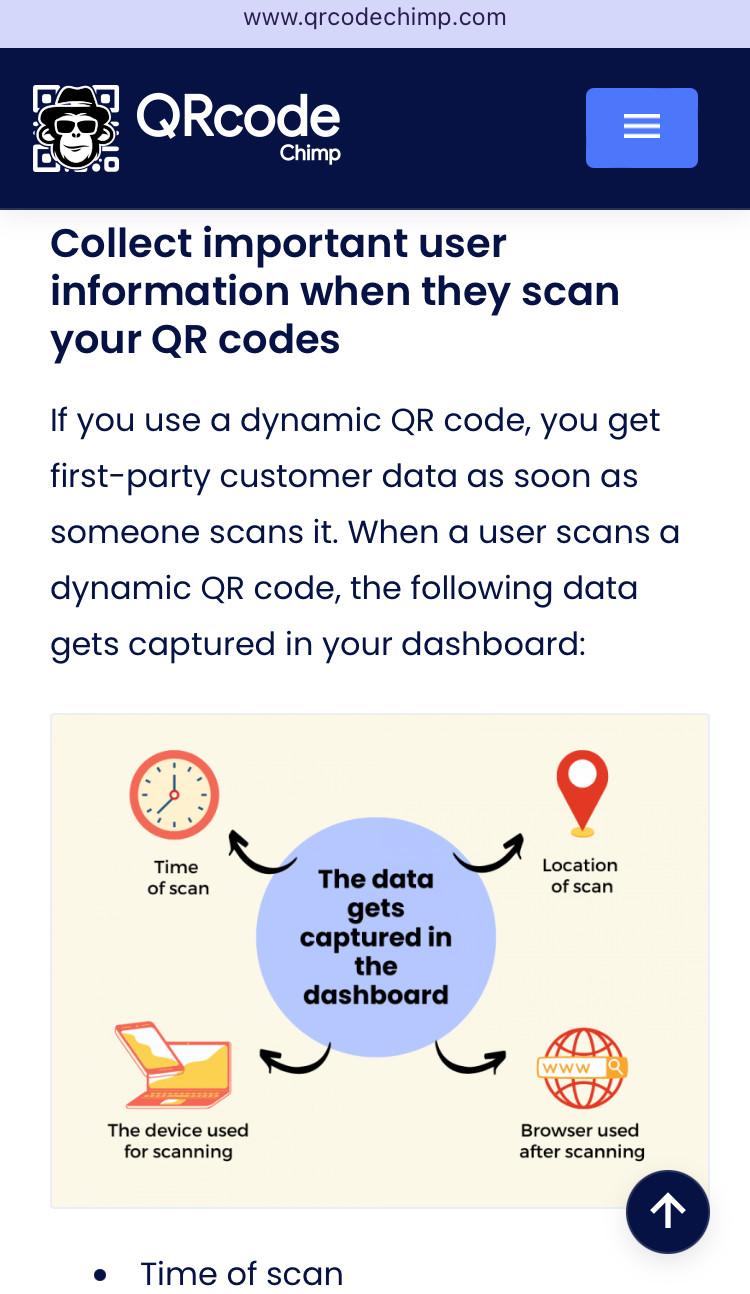
Here's an article *promoting* the use of QR codes to collect data. Just by scanning the code, you are potentially giving up data.
https://www.qrcodechimp.com/collect-first-party-data-with-qr-codes/Screenshot below is from the article.
Do not normalize using QR codes. All important information should be on the flyer, maybe with a QR code in the corner for people who want this. Have the URL printed out as well. The other thing to consider is that it is easy to create a fake URL that looks legitimate (e.g. with Cyrillic characters) and will fool most people at a glance. These fake URLs may even have a valid security certificate! Manually typing in the URL mostly bypasses this problem.
-
Chrisshy Keygenreplied to Nazi trumps fuck off. last edited by
@Mikal @CrimethInc a QR code is EXACTLY as opaque and trackable as a link on a webpage.
What needs to become normalized is looking at the URL provided, and having the resources to think critically before visiting
-
Nazi trumps fuck off.replied to Chrisshy Keygen last edited by
Look up homograph attack. If you point at a QR code and it comes up with a Cyrillic character, it's easy to get fooled. But if you type the printed URL in, chances are you're using a standard English language keyboard and will type the legitimate URL in.
Scanning QRs reduces this friction at the cost of security. It has the benefit of ease of engagement, but you have to recognize the trade offs and consider who your average user is.
Also, even legit sites may be collecting data on you that isn't obvious.
-
Chrisshy Keygenreplied to Nazi trumps fuck off. last edited by
@Mikal @CrimethInc right, but what I am saying is that every link on the web has a very similar threat profile.
The main difference is that a QR can be tampered with; which IS valid.
The IDN homograph is interesting, but at this point every browser has mitigations and if you look at a URL with mixed characters it's going to really messed up

