tandy put their sound chip on the 1A interrupt?
-
replied to Foone🏳️⚧️ last edited by
ooh, I'd also need to be able to watch multiple address ranges at once. that'd be sweet, multiple windows of visibility into RAM
-
replied to Foone🏳️⚧️ last edited by
I'm in Paris, I look at work ram, I see the image of the Eiffel. I head to Rome, and before I load the next image, I can see that the Eiffle tower in workram now has the wrong stride.
That's odd, because it means it had to rewrite the image in memory, the image it's about to unload. -
replied to Foone🏳️⚧️ last edited by
I think this might be the GUI system doing a screenshot of the image under a window, so it can restore it at the end. And it still does that here, even though we'll never need to restore that image: we're about to overwrite it
-
replied to Foone🏳️⚧️ last edited by
Here's what I want a tool to do:
I hit a breakpoint in the debugger, I turn it on, set another breakpoint, and hit go.
between those two breakpoints, every time a CALL instruction is hit, it dumps my selected memory region. If it's identical to the last dump, it's ignored.
At the end, each dump is rendered as an image, and the combined set are an animation I can scroll through. -
replied to Foone🏳️⚧️ last edited by
I need a higher order debugger. I'm doing too much shit manually
-
replied to Foone🏳️⚧️ last edited by
@foone not sure if you could use it for older programs, but have you ever used Time Travel Debugging?
-
replied to Foone🏳️⚧️ last edited by
GOT YOU, YOU SON OF A BITCH! I FOUND YOU.
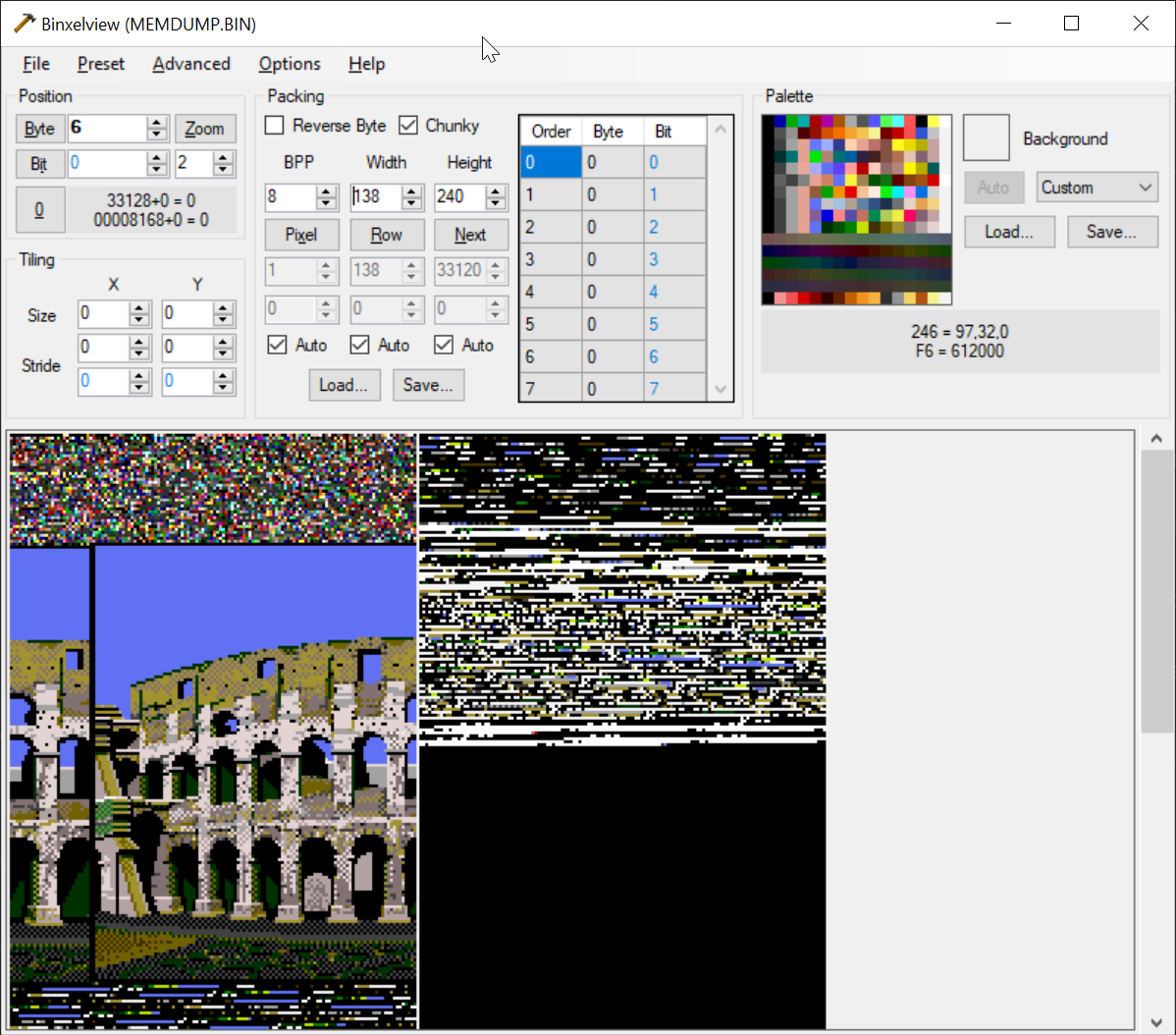
-
replied to Foone🏳️⚧️ last edited by
it's in a function I already found, temporarily named "blit_related".
I guess they don't decode the image until RIGHT before it needs to go up on the screen!
-
replied to Foone🏳️⚧️ last edited by
if definitely decompresses and then blits the image as two parts, which aren't evenly sized, and it starts from the bottom
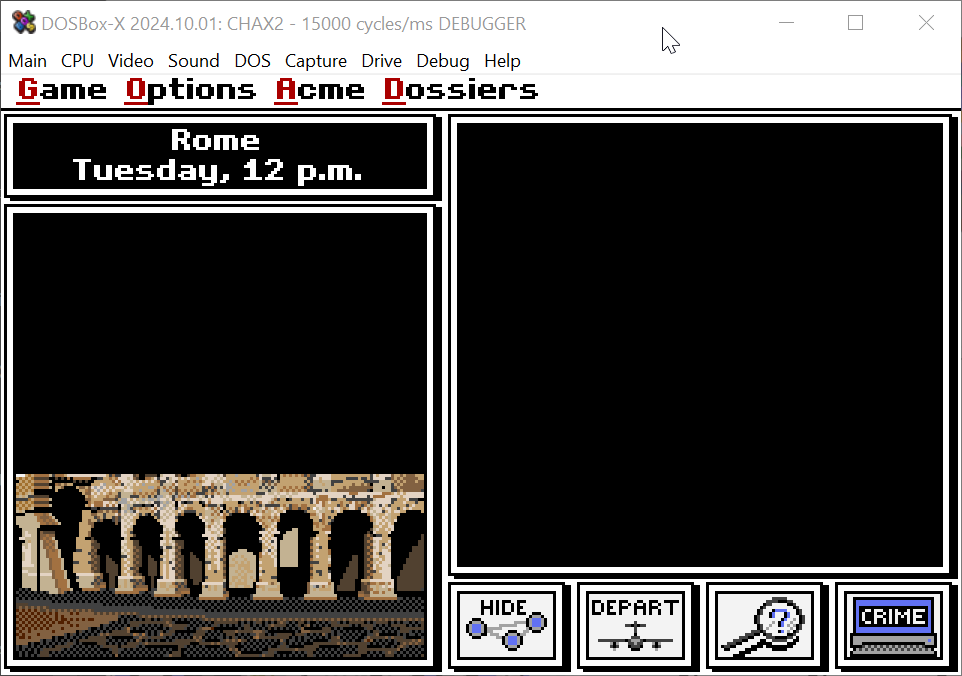
-
replied to Foone🏳️⚧️ last edited by
I think they're just trying to keep their RAM usage down by not having both halves in memory at once
-
replied to Foone🏳️⚧️ last edited by
@foone this sounds like a job for whatever scripting the debugger supports?
-
replied to a kilo of saucepans (rakslice) last edited by
@rakslice
new side project: add scripting to this debugger -
replied to Foone🏳️⚧️ last edited by
wait is this image format vertically interlaced!?
-
replied to Foone🏳️⚧️ last edited by
It loads the half-width version, then a few functions later, it's been replaced with a full-width version.
Strange!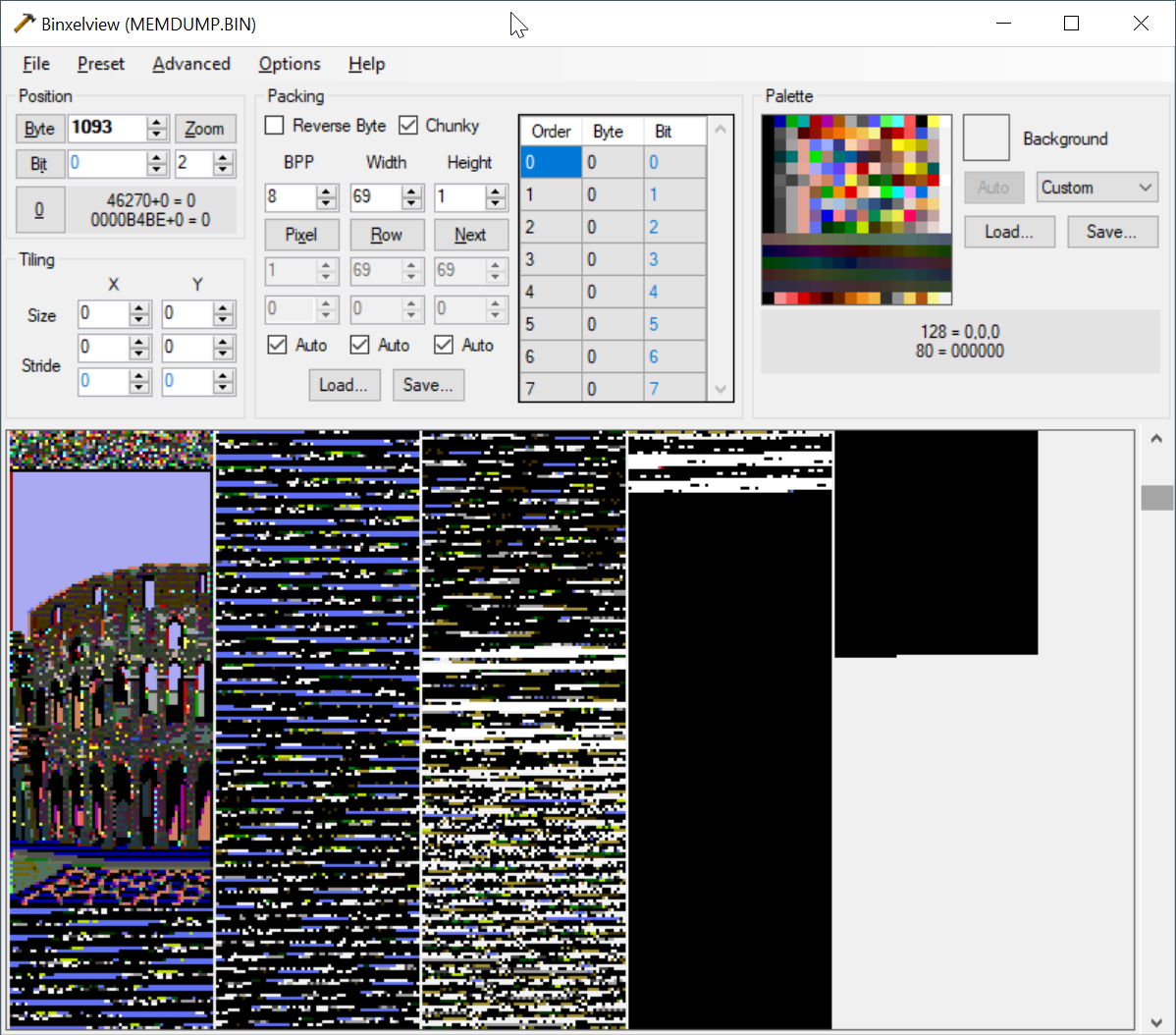
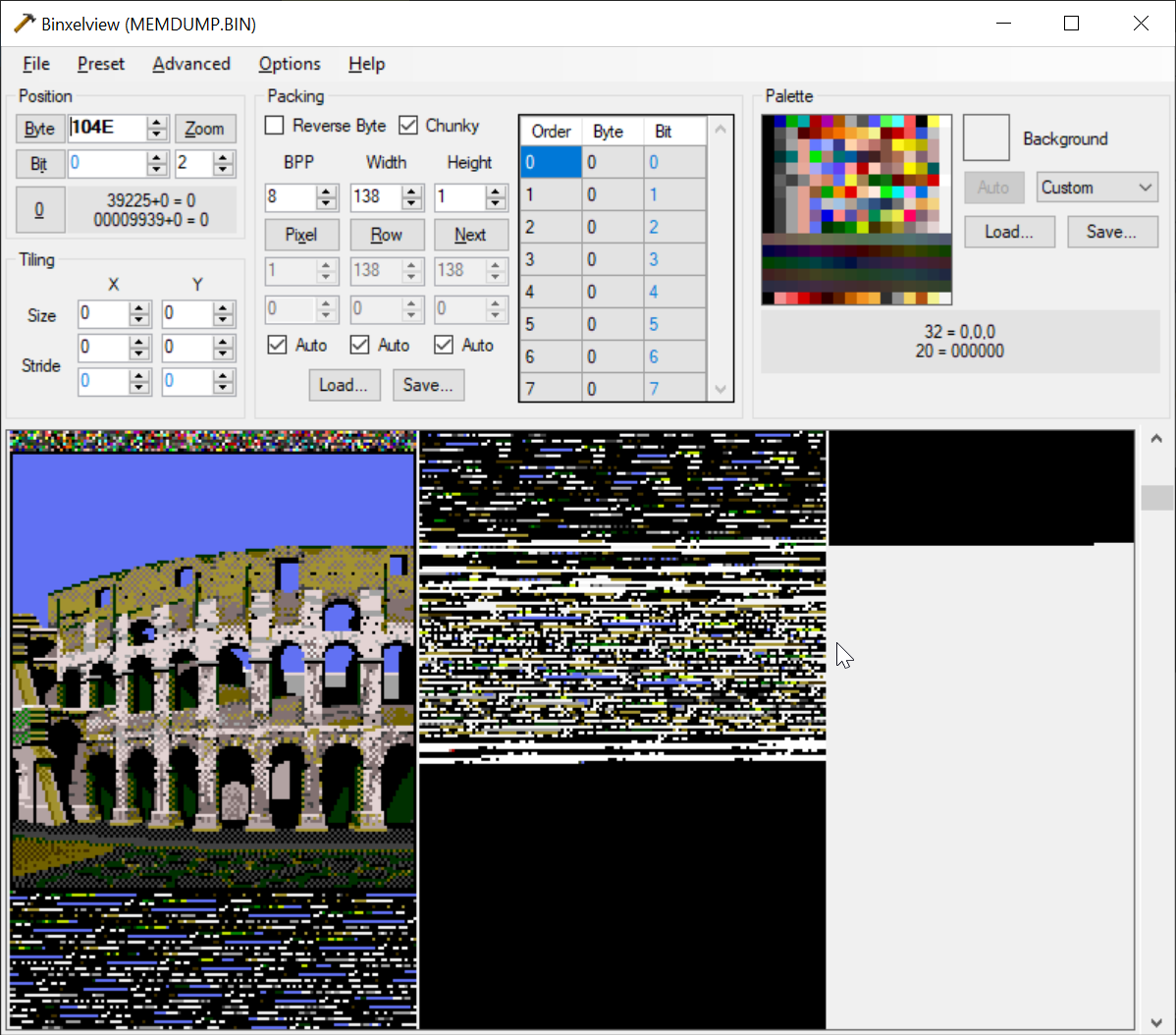
-
replied to Foone🏳️⚧️ last edited by
wait no, the colors are wrong... I bet I'm seeing it decompress the binary, but that's using the full width of the bytes. it then gets expanded out to a 16-color image.
-
replied to Foone🏳️⚧️ last edited by
well the good news is that I think I've found the decompress_image function. the bad news is that now I have to reverse engineer it

-
replied to Foone🏳️⚧️ last edited by
it's currently doing the obvious thing for a decompressor to do:
write the byte 04 every 69 bytes -
replied to Foone🏳️⚧️ last edited by
oh sweet jesus, that's the left two pixels of the image.
it's loading the image vertically!at least it's top to bottom.
-
replied to Foone🏳️⚧️ last edited by
yeah, doom did that too, but Doom was a 2.5D image that had to do pseudo-raycasting.
THIS GAME DOES NOT
