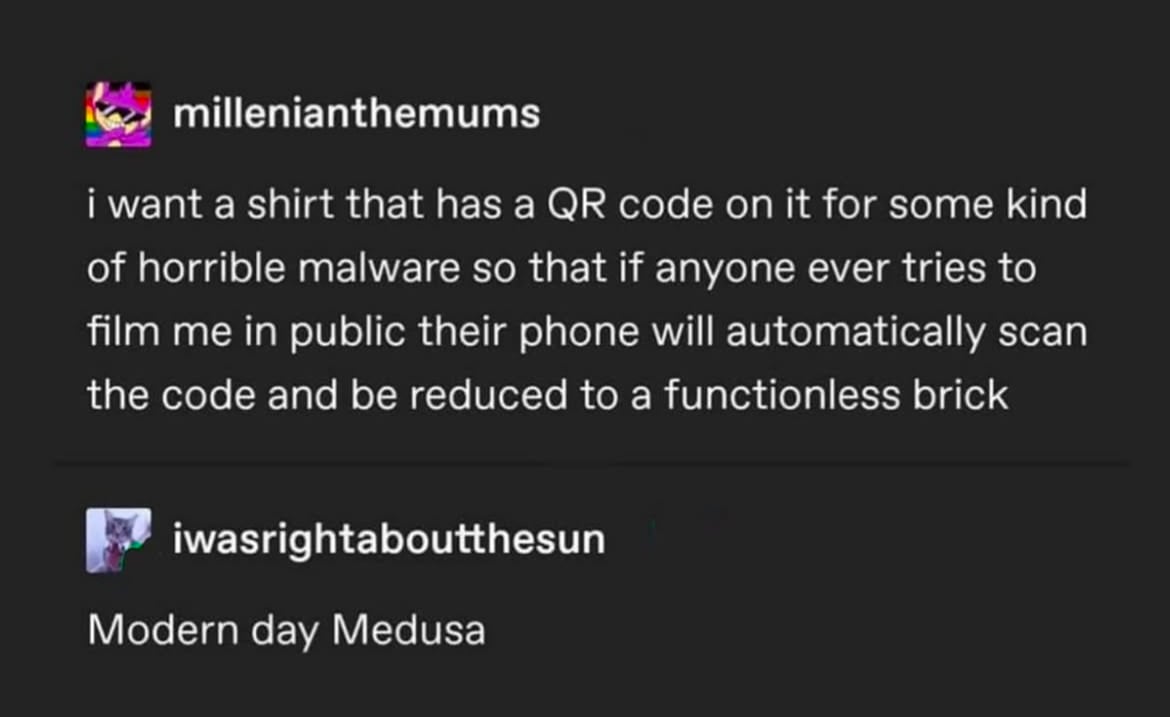
The best use of QR codes
-
[email protected]replied to [email protected] last edited by
You're right, I must have been thinking of something else. Happily I can't find any chatter about actual malware in QR codes (it's all redirecting to malicious websites), though obviously there's always the possibility of a new exploit being discovered.
-
[email protected]replied to [email protected] last edited by
The 3DS used to be hacked using a QR code that was scanned using the game cubic ninja (it used QR codes as a medium for sharing levels). The interpreter had a basic memory safety bug, so you could trigger a ROP chain using a malformed QR code to get ACE. This was of course voluntary by the user (and cubic ninja was hard to get because it was not a commercial success) but that qualifies, I guess.
Then they found out the 3ds browser uses a WebKit version from 2003 and nowadays you just go to a website lol
-
I'd be flattered if someone wanted to film me with their phone.

-
[email protected]replied to [email protected] last edited by
Jobs @[email protected] got fired from:
-
[email protected]replied to [email protected] last edited by
ACE on a WiiU is just as easy, at least with the Wii you had to use a game!
-
[email protected]replied to [email protected] last edited by
So what? That only prevents people from editing the photo in certain programs like Adobe Photoshop.
-
[email protected]replied to [email protected] last edited by
ICBM launch control operator
-
[email protected]replied to [email protected] last edited by
- Submariner
-
[email protected]replied to [email protected] last edited by
Professional Mornington Crescent player
-
Well that's one layer, but when you decode a url, you're probably going to get a url, and then it's going to go to that url
So now you just made them to to a website. What's there? Whatever you want. Maybe you ask them for Facebook/Google/GitHub or whatever authorization to see their name and email, which a lot of people would do. Then redirect them to a page saying "now I know who you are, delete the photo, <user>"
Or you could send them a payload based on fingerprinting their request, you could give them a fake page to steal their password, etc