I sent a patch to make openssh do a fun thing! (Do not use this on its own, it really needs more infrastructure that I've written but haven't tested but I want to make sure this is something people actually want first) https://lists.mindrot.org/piperma...
-
I sent a patch to make openssh do a fun thing! (Do not use this on its own, it really needs more infrastructure that I've written but haven't tested but I want to make sure this is something people actually want first) https://lists.mindrot.org/pipermail/openssh-unix-dev/2024-October/041618.html
-
Matthew Garrettreplied to Matthew Garrett on last edited by
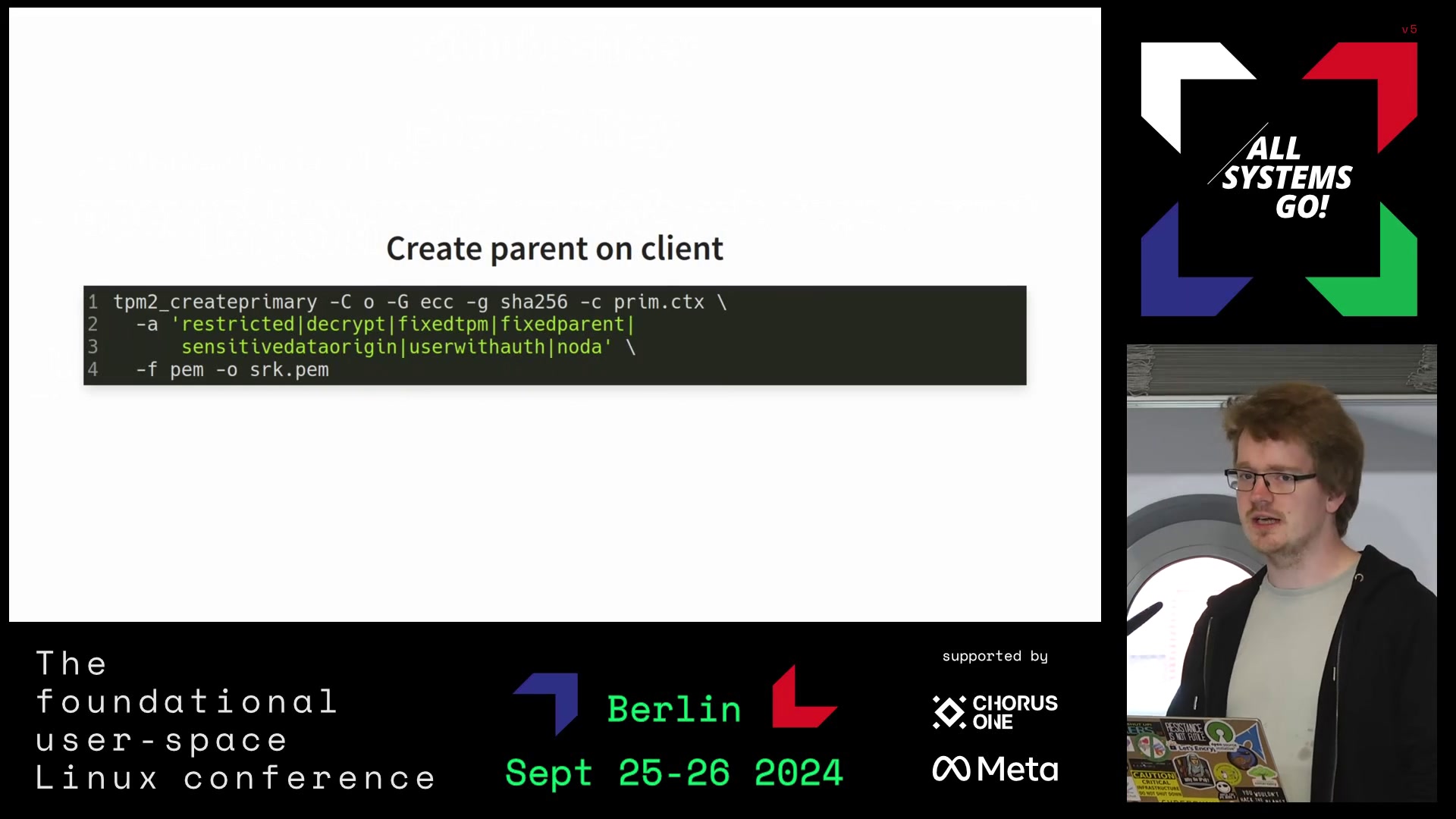
I have, horrifyingly, also just figured out a way to tie TPM-based key attestation into SSH certificates such that you can verify that an SSH host key is hardware backed
-
@mjg59 Do you have pointers on that? For use with the RFC9200 ACE framework, this might come in handy.
-
@chrysn embed the ekcert, ak and credential activation and key attestation blobs in the cert, have an Authorized principals command verify them and ensure they validate the host pubkey
-
@mjg59 @chrysn Instead of doing it in one go (as it reads like that now), the attestation verification could be performed by the CA which only mints the SSH cert (possibly with some custom extension added) when the TPM remote attestation verification succeeds. Then the host only needs to trust the CA (assuming it’s honest). This is an implementation of the CA part: https://github.com/Foxboron/ssh-tpm-ca-authority
-
For the people interested there is an ASG2024 and a bsides oslo talk on this project now.
SSH authentication using user and machine identities
Strong authentication requires multiple signals: identity claims proves that identity of the person, while device attestation proves poss...

(media.ccc.de)
Still very much a POC thing though.
