I cannot believe this completely unsupported fan-made utility from 1997 is failing to work on modern windows
-
"This is a beta version which will expire on February 1, 2007."
uh-oh
-
it lives! textures and flat shading and gouraud shading don't work, but at least I can tell what the object actually is!
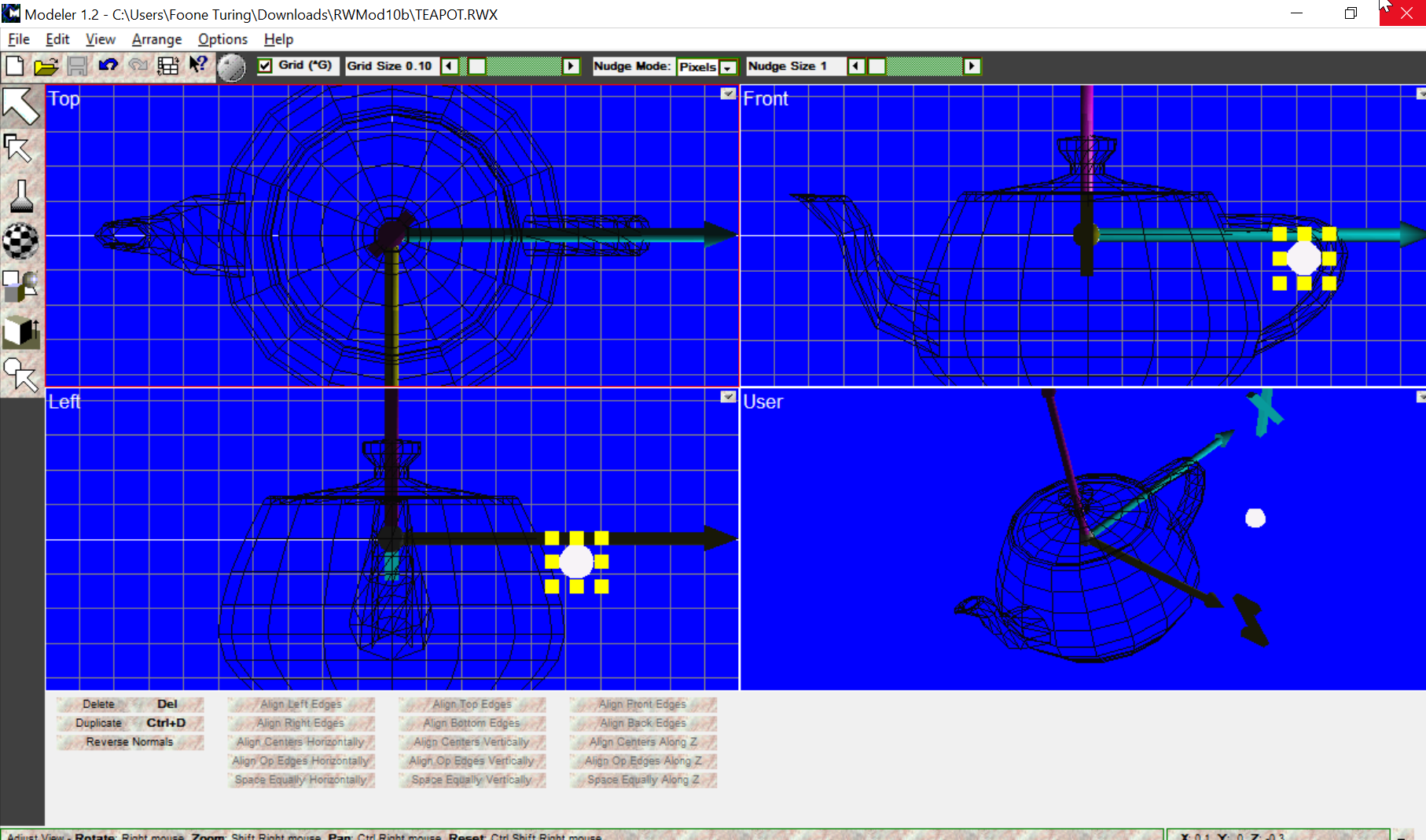
-
and after getting this to work (I had to get a leaked beta of an unreleased version, add specific renderware DLLs, then crack that version so it'd run after 2007!) it turns out it can't open the file I DOWNLOADED THIS WHOLE PROGRAM FOR
-
at least I can diff the EXEs
-
they changed ONE BYTE
-
yep. they changed a JNC to a JMP. that's all.
-
that's the fun thing about cracking software! You can often do it by changing one byte, or less (I've cracked games with 1 bit different).
but the trick is figuring out which byte to change
-
but the tl;dr for how classic cracking works.
You find the spot in the program that looks like this:
if (is_pirated()){
printf("NO WAREZ!\n");
exit(-1);
}in the disassembly (on x86, at least) that'll look something like:
CALL (address of is_pirated)
TEST EAX, EAX
JZ (address of rest of the game)
(some code to yell at the pirate) -
@foone Have you ever paid for your WinRAR license?
-
the return code of is_pirated is in EAX (in cdecl calling convention). test EAX,EAX compares it against itself so the status flags are set, and then JZ jumps if the Zero Flag is set.
Basically, if is_pirated returned 0, we jump to the game, otherwise we yell at the pirate and quit.
-
so you just change the conditional JZ to an unconditional JMP.
Now we call is_pirated, but no matter what it returned (0, 1, 3.14159, or "hello world"), we jump to the rest of the game. -
And what's the difference between how you encode JZ vs JMP?
One byte:E9 71 JMP +71
74 71 JZ +71 -
so you patch exactly one byte and now the pirated game works.
-
@cr1901 No. I have paid for WinZip though, technically. I bought a used copy in a bunch of compute crap
-
Foone🏳️⚧️replied to Foone🏳️⚧️ last edited by [email protected]
a significant amount of all anti-cracking development in the last 45 years is figuring out ways to make it impossible to crack a game with just one byte.
-
The main ways to do this boil down to:
1. You layer or repeat the checks. now you gotta patch multiple places, in different ways, and what if you miss one? you're still fucked!
2. You don't have this check at all. Derive some constants from the check results and now all the levels load inside out and upside down, or something. This just makes it harder to figure out where to patch.
3. Forget it, and you protect your software elsewhere: hardware, OS DRM layers, etc. -
@foone Can we automate changing each byte to a NOP until we find the one that works? Think brute-forcer, not smarter.
-
@crobbler I am currently working on a system to do basically that, to reverse engineer DOS games by randomly corrupting them in parallel
-
Anyway back to hacking this Renderware-using game. So, I can't load the models. Why not? Are they fundamentally different, like they're encrypted or compressed? are they just the wrong version number? can we hack the version number?
-
Foone🏳️⚧️replied to Foone🏳️⚧️ last edited by [email protected]
arg, all my renderware models on hand are either the .RWB ones from the game that don't work, or they're .RWX from the Modeller. RWB is a binary compiled version of RWX, but they're completely different
