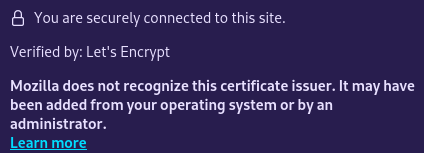
Well, this is interesting. #LetsEncrypt #Firefox #Mozilla
-
Jiří Eischmann :fedora:replied to Scott Williams 🐧 on last edited by
@vwbusguy Is it a distro-provided Firefox?
-
Wilmar Igl, PhDreplied to Scott Williams 🐧 on last edited by
@vwbusguy Weird, fixed it?
-
Scott Williams 🐧replied to Jiří Eischmann :fedora: on last edited by
@sesivany Yes, Fedora - I'm guessing related to this:

Shortening the Let's Encrypt Chain of Trust
When Let’s Encrypt first launched, we needed to ensure that our certificates were widely trusted. To that end, we arranged to have our intermediate certificates cross-signed by IdenTrust’s DST Root CA X3. This meant that all certificates issued by those intermediates would be trusted, even while our own ISRG Root X1 wasn’t yet. During subsequent years, our Root X1 became widely trusted on its own. Come late 2021, our cross-signed intermediates and DST Root CA X3 itself were expiring.
(letsencrypt.org)
The server is also running an updated Fedora 39 and the cert was issued there from certbot.
-
Scott Williams 🐧replied to Scott Williams 🐧 on last edited by
@sesivany For the record, the website still works *because* Fedora still trusts the CA. Mozilla seems to have taken the strict route where Fedora took the path of "let's not break half the internet for our users".
-
Scott Williams 🐧replied to Wilmar Igl on last edited by [email protected]
@wiligl I think it's related to this:

Shortening the Let's Encrypt Chain of Trust
When Let’s Encrypt first launched, we needed to ensure that our certificates were widely trusted. To that end, we arranged to have our intermediate certificates cross-signed by IdenTrust’s DST Root CA X3. This meant that all certificates issued by those intermediates would be trusted, even while our own ISRG Root X1 wasn’t yet. During subsequent years, our Root X1 became widely trusted on its own. Come late 2021, our cross-signed intermediates and DST Root CA X3 itself were expiring.
(letsencrypt.org)
Buckle up - it's gonna be an interesting year for TLS.
-
Marcos Dionereplied to Scott Williams 🐧 on last edited by
-
Glowing Cat of the Nuclear Wastelands ☣replied to Scott Williams 🐧 on last edited by
@[email protected] can you reproduce this on other sites secured with let's encrypt? I just checked one of my sites using one of their certs and Firefox for Android is just fine?
I have noticed in the past that occasionally it's a little slow to recognize when a new cert is installed, particularly when it's the first time being issued for a domain. -
Scott Williams 🐧replied to Scott Williams 🐧 on last edited by
-
Scott Williams 🐧replied to Marcos Dione on last edited by
-
Scott Williams 🐧replied to Glowing Cat of the Nuclear Wastelands ☣ on last edited by [email protected]
@deathkitten Yes. Keep in mind that if the CA is in the OS trust store (ie, Android in this case), then the page will still work. It only shows this notice when you inspect the cert.
None of these are for newly issued certs, but I did just renew one for good measure and still got the warning with the renewed cert.
-
Scott Williams 🐧replied to Scott Williams 🐧 on last edited by
@deathkitten So far, I'm able to reproduce it with #LetsEncrypt certs issued from #certbot, #caddy, and #certmanager, both fresh and a month or two old.
Firefox 123.0.1 doesn't trust any of them.
Again, it still works because the OS CA trust includes it, so most users won't notice anything broken (yet).
-
Scott Williams 🐧replied to Scott Williams 🐧 on last edited by
Ironically, when it looked like this was going to break #Chrome the solution was to use #Firefox.

Shorting the chain of trust
I just read the post about the decision of Let's Encrypt to drop backward compatibility with older Android systems. Shortening the Let's Encrypt Chain of Trust - Let's Encrypt What happens is you start getting certifica…

Let's Encrypt Community Support (community.letsencrypt.org)
-
Glowing Cat of the Nuclear Wastelands ☣replied to Scott Williams 🐧 on last edited by
@[email protected] I looked at the cert for both a personal site and the instance I'm posting on, both from Firefox for Android and Firefox developer edition. I'm not seeing this anywhere. I also had an update waiting on the Developer edition, and saw the same thing before and after restart to upgrade.
I'm not sure how ibe.social gets its Let's Encrypt cert, but I know the one on my personal site uses whatever bespoke thing that Dreamhost set up in its control panel to get certificates for their customers.
Can you let me know one or more of the domains you're seeing this on, so I can look in my browser? If you want to see the domains I've checked from my end, it would be sfintel.space and ibe.social -
Scott Williams 🐧replied to Glowing Cat of the Nuclear Wastelands ☣ on last edited by
@deathkitten What's weird is, I'm able to reproduce it with Firefox 123.1 and 124 on multiple systems, but not *all* of them. I get this message from Fedora Workstation 39 and Fedora Kinoite 39, but I don't with Fedora Atomic Budgie 39.
It seems to be all LE sites, AFAICT, when it happens. Tried with certs generated from certbot, caddy server, and cert-manager.
-
Glowing Cat of the Nuclear Wastelands ☣replied to Scott Williams 🐧 on last edited by
@[email protected] Is this just regular Firefox, Developer edition, or something else?
For data collection purposes, I'm using developer edition 125.0b4 (64-bit) on pop_OS!
I hope this is just a wrinkle that'll get sorted shortly, because if this is an indication of some sort of falling out between Firefox/Mozilla and Let's Encrypt, it's going to be a major problem considering how many sites out there are using Let's Encrypt. Especially in light of the bullshit anti-Ad blocker changes that Google has coming for Chrome. >.< -
Marcos Dionereplied to Scott Williams 🐧 on last edited by
@vwbusguy @sesivany Well, they used to have an intermediate certificate C signed by root A and root B¹. Then A expired (the CentOS 6 thing I mention), then C did or was simply replaced by intermediate D, signed only by B.
If I get it right from the error message, you OS trusts B _but ffox doesn't_?
¹ reading that I start to suspect it doesn't make any sense.
-
Scott Williams 🐧replied to Glowing Cat of the Nuclear Wastelands ☣ on last edited by [email protected]
@deathkitten It's regular Firefox from the Fedora update repositories. Tested on three different Fedora 39 variants on two different networks.
The fact that I don't see it on the same Firefox version with Budgie Atomic but I do with Kinoite is very strange, since they're both Atomic from the same rpm source.
-
Scott Williams 🐧replied to Scott Williams 🐧 on last edited by [email protected]
I'm able to reproduce this with Firefox 123.0.1 and Firefox 124.0 on two different systems on two different networks, but wasn't able to reproduce it on a third with Firefox 121 or 124.
I got the message with Fedora Workstation 39 and Kinoite 39 but not Budgie Atomic 39. 🫠
I tested with certs generated from certbot, cert-manager, and caddy, both freshly renewed and months old and these all behaved the same.
-
Raptor :gamedev:replied to Scott Williams 🐧 on last edited by
@vwbusguy it's gotta be something with a setting, could it be from the enterprise CA management settings? i'm not getting it on my installs of the same versions from a vanilla source build.