v3.10.0 -> 3.10.1 upgrade error
-
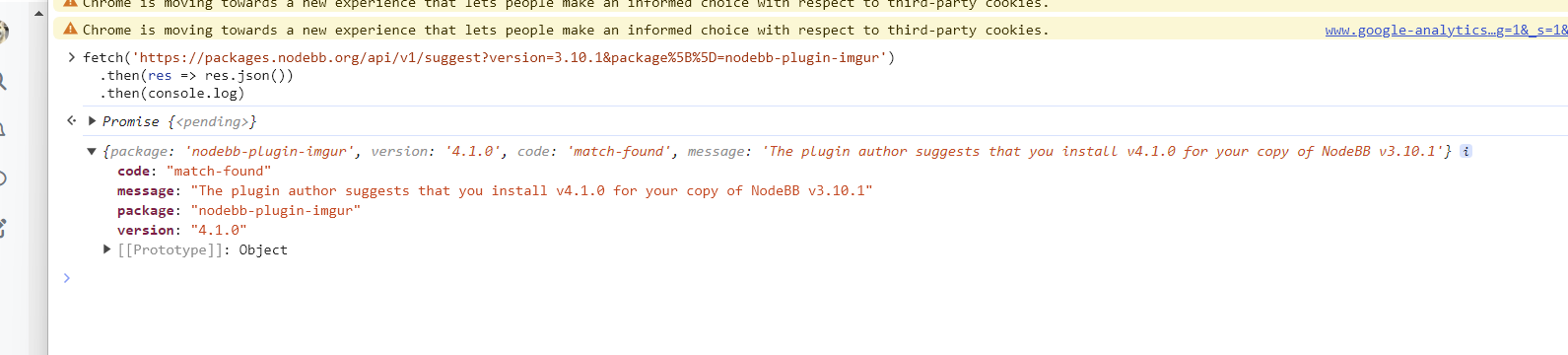
looks like a cors issue:
< Promise {status: "pending"} [Error] Origin https://support.sweetpproductions.com is not allowed by Access-Control-Allow-Origin. Status code: 404 [Error] Fetch API cannot load https://packages.nodebb.org/api/v1/suggest?version=3.10.1&package%5B%5D=nodebb-plugin-imgur due to access control checks. [Error] Failed to load resource: Origin https://support.sweetpproductions.com is not allowed by Access-Control-Allow-Origin. Status code: 404 (suggest, line 0) [Error] Unhandled Promise Rejection: TypeError: Load failed -
when I ssh into my server I get this:
root@server:~# curl -I https://packages.nodebb.org curl: (60) SSL: no alternative certificate subject name matches target host name 'packages.nodebb.org' More details here: https://curl.se/docs/sslcerts.html curl failed to verify the legitimacy of the server and therefore could not establish a secure connection to it. To learn more about this situation and how to fix it, please visit the web page mentioned above. root@server:~#This happens on 2 seperate VPS servers I manage.
on my local device I see this:
curl -I https://packages.nodebb.org HTTP/1.1 302 Found Server: nginx/1.18.0 (Ubuntu) Date: Wed, 09 Oct 2024 18:59:39 GMT Content-Type: text/plain; charset=utf-8 Content-Length: 28 Connection: keep-alive X-Powered-By: Express Access-Control-Allow-Origin: * Location: /stats Vary: AcceptSomething interesting, when I run the command on my local device running through a VPN I get the same error shown for my 2 remote VPS's
-
Same problem.
3. Checking installed plugins for updates...Checking installed plugins and themes for updates... Warning: An unexpected error occured when attempting to verify plugin upgradability Error occurred during upgrade: TypeError: fetch failed at node:internal/deps/undici/undici:13185:13 at process.processTicksAndRejections (node:internal/process/task_queues:95:5) at async call (/home/user_radforum/nodebb/src/request.js:37:19) at async getSuggestedModules (/home/user_radforum/nodebb/src/cli/upgrade-plugins.js:78:27) at async checkPlugins (/home/user_radforum/nodebb/src/cli/upgrade-plugins.js:101:27) at async upgradePlugins (/home/user_radforum/nodebb/src/cli/upgrade-plugins.js:125:17) at async Object.handler (/home/user_radforum/nodebb/src/cli/upgrade.js:29:4) at async runSteps (/home/user_radforum/nodebb/src/cli/upgrade.js:55:5) at async Object.runUpgrade [as upgrade] (/home/user_radforum/nodebb/src/cli/upgrade.js:98:3) 2024-10-09T19:00:50.732Z [4568/271155] - error: uncaughtException: fetch failed TypeError: fetch failed at node:internal/deps/undici/undici:13185:13 at process.processTicksAndRejections (node:internal/process/task_queues:95:5) at async call (/home/user_radforum/nodebb/src/request.js:37:19) at async getSuggestedModules (/home/user_radforum/nodebb/src/cli/upgrade-plugins.js:78:27) at async checkPlugins (/home/user_radforum/nodebb/src/cli/upgrade-plugins.js:101:27) at async upgradePlugins (/home/user_radforum/nodebb/src/cli/upgrade-plugins.js:125:17) at async Object.handler (/home/user_radforum/nodebb/src/cli/upgrade.js:29:4) at async runSteps (/home/user_radforum/nodebb/src/cli/upgrade.js:55:5)My nodebb version is 3.9 and i try to update to 3.10.1
-
I got
~/nodebb$ dig packages.nodebb.org ; <<>> DiG 9.18.28-1~deb12u2-Debian <<>> packages.nodebb.org ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 50858 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;packages.nodebb.org. IN A ;; ANSWER SECTION: packages.nodebb.org. 300 IN A 138.197.166.38 ;; Query time: 12 msec ;; SERVER: 185.12.64.2#53(185.12.64.2) (UDP) ;; WHEN: Wed Oct 09 21:42:10 CEST 2024 ;; MSG SIZE rcvd: 64 -
root@server:~# dig packages.nodebb.org +short 138.197.166.38root@server:~# dig packages.nodebb.org less ; <<>> DiG 9.18.28-0ubuntu0.24.04.1-Ubuntu <<>> packages.nodebb.org less ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23609 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 13 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 65494 ;; QUESTION SECTION: ;packages.nodebb.org. IN A ;; ANSWER SECTION: packages.nodebb.org. 108 IN A 138.197.166.38 ;; AUTHORITY SECTION: nodebb.org. 108 IN NS greg.ns.cloudflare.com. nodebb.org. 108 IN NS sue.ns.cloudflare.com. ;; ADDITIONAL SECTION: greg.ns.cloudflare.com. 108 IN A 173.245.59.115 greg.ns.cloudflare.com. 108 IN A 172.64.33.115 sue.ns.cloudflare.com. 108 IN A 108.162.192.145 greg.ns.cloudflare.com. 108 IN AAAA 2606:4700:58::adf5:3b73 sue.ns.cloudflare.com. 108 IN AAAA 2803:f800:50::6ca2:c091 sue.ns.cloudflare.com. 108 IN A 173.245.58.145 sue.ns.cloudflare.com. 108 IN AAAA 2a06:98c1:50::ac40:2091 greg.ns.cloudflare.com. 108 IN A 108.162.193.115 greg.ns.cloudflare.com. 108 IN AAAA 2803:f800:50::6ca2:c173 greg.ns.cloudflare.com. 108 IN AAAA 2a06:98c1:50::ac40:2173 ; <<>> DiG 9.18.28-0ubuntu0.24.04.1-Ubuntu <<>> packages.nodebb.org ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 52811 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 13 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 65494 ;; QUESTION SECTION: ;packages.nodebb.org. IN A ;; ANSWER SECTION: packages.nodebb.org. 86 IN A 138.197.166.38 ;; AUTHORITY SECTION: nodebb.org. 86 IN NS greg.ns.cloudflare.com. nodebb.org. 86 IN NS sue.ns.cloudflare.com. ;; ADDITIONAL SECTION: sue.ns.cloudflare.com. 86 IN A 173.245.58.145 sue.ns.cloudflare.com. 86 IN A 172.64.32.145 greg.ns.cloudflare.com. 86 IN AAAA 2606:4700:58::adf5:3b73 sue.ns.cloudflare.com. 86 IN AAAA 2803:f800:50::6ca2:c091 greg.ns.cloudflare.com. 86 IN A 173.245.59.115 greg.ns.cloudflare.com. 86 IN A 172.64.33.115 sue.ns.cloudflare.com. 86 IN AAAA 2606:4700:50::adf5:3a91 sue.ns.cloudflare.com. 86 IN A 108.162.192.145 greg.ns.cloudflare.com. 86 IN A 108.162.193.115 greg.ns.cloudflare.com. 86 IN AAAA 2a06:98c1:50::ac40:2173 sue.ns.cloudflare.com. 86 IN AAAA 2a06:98c1:50::ac40:2091 greg.ns.cloudflare.com. 86 IN AAAA 2803:f800:50::6ca2:c173 ;; Query time: 0 msec ;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP) ;; WHEN: Wed Oct 09 21:44:20 CEST 2024 ;; MSG SIZE rcvd: 382 -
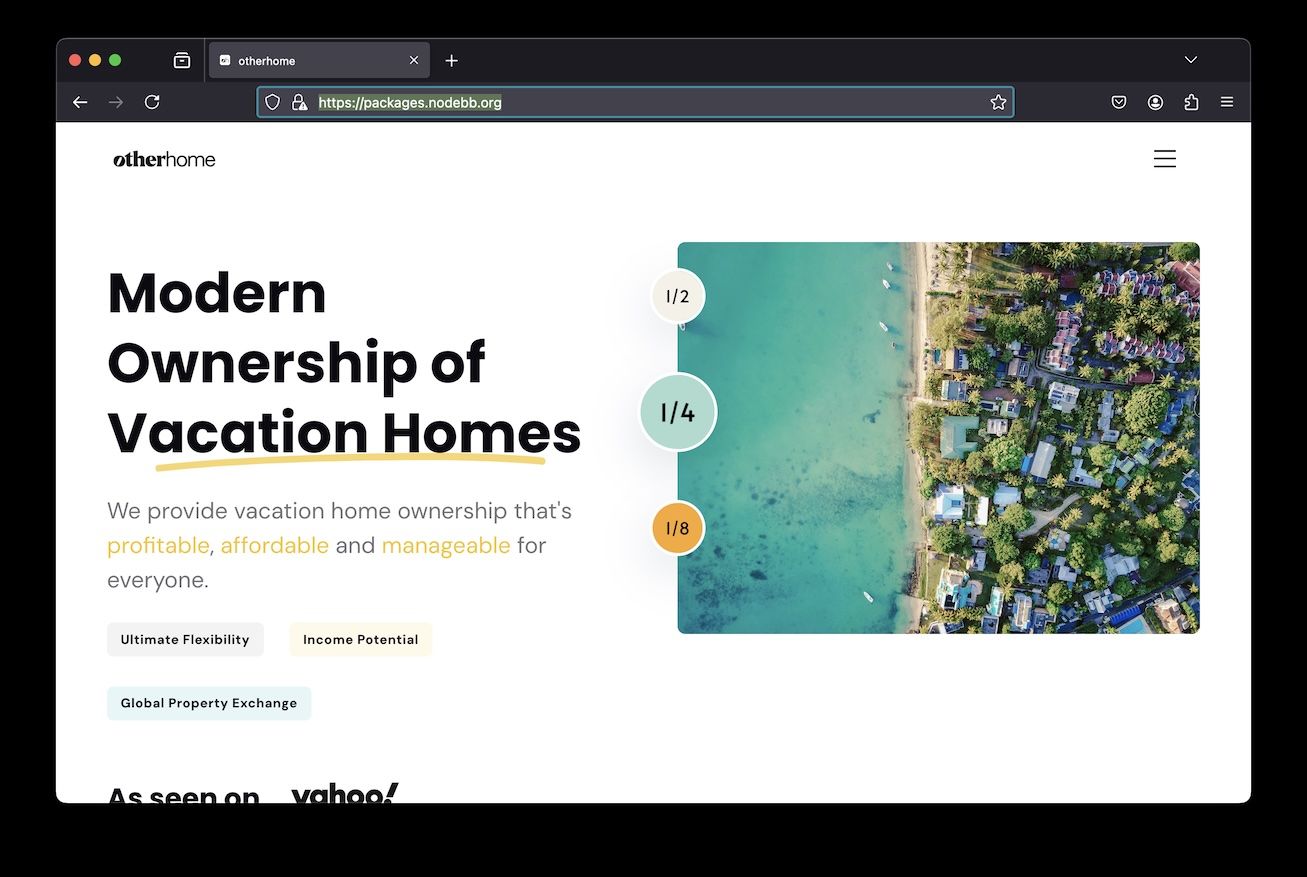
@Julian https://packages.nodebb.org loads this url: otherhome.ca
-
For me it looks like a misconfiguration certificate
~/nodebb$ openssl s_client -connect packages.nodebb.org:443 CONNECTED(00000003) depth=2 C = US, O = Internet Security Research Group, CN = ISRG Root X1 verify return:1 depth=1 C = US, O = Let's Encrypt, CN = R11 verify return:1 depth=0 CN = otherhome.ca verify return:1 --- Certificate chain 0 s:CN = otherhome.ca i:C = US, O = Let's Encrypt, CN = R11 a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256 v:NotBefore: Sep 30 11:40:17 2024 GMT; NotAfter: Dec 29 11:40:16 2024 GMT 1 s:C = US, O = Let's Encrypt, CN = R11 i:C = US, O = Internet Security Research Group, CN = ISRG Root X1 a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256 v:NotBefore: Mar 13 00:00:00 2024 GMT; NotAfter: Mar 12 23:59:59 2027 GMT --- Server certificate -----BEGIN CERTIFICATE----- MIIE+TCCA+GgAwIBAgISBKFrGq/uYt1x2fT4nxpBycwnMA0GCSqGSIb3DQEBCwUA MDMxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MQwwCgYDVQQD EwNSMTEwHhcNMjQwOTMwMTE0MDE3WhcNMjQxMjI5MTE0MDE2WjAXMRUwEwYDVQQD EwxvdGhlcmhvbWUuY2EwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCx QM9xk/KQ/V60FHRXJywIpVnbmH8PNDSHMGx5XIEHdiw035J+DFySEkuXYdlgV8tH fENKbIMz+Ydy2sr9aniOZ469QrU/IS2pQn+qM51rvMLrgG7Jj4rqT0DHPTWg+bPK hyDHSipG7OfI2MeSL5FCJ8reZJHgidU3M+TE7oEaS6vbtIzAgR96SNtv5HQHzjkp 3f7iLtoY9Dg2O4aSEwqqz6GhwlgVwQTOok43YWR0IP99ZKm1xplh7Zaa8rwybD3u jEE7MjxDz3A7Dz9nNOXlZz37qywh4Z3SUD4T/FPT0vxqiHoqZ/sn+arKiWHmL2Rq RNGqu3SdXUQ/V4kg/euhAgMBAAGjggIhMIICHTAOBgNVHQ8BAf8EBAMCBaAwHQYD VR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMAwGA1UdEwEB/wQCMAAwHQYDVR0O BBYEFNK/bs9ALNV6hDhxJuBzFuPOiN7WMB8GA1UdIwQYMBaAFMXPRqTq9MPAemyV xC2wXpIvJuO5MFcGCCsGAQUFBwEBBEswSTAiBggrBgEFBQcwAYYWaHR0cDovL3Ix MS5vLmxlbmNyLm9yZzAjBggrBgEFBQcwAoYXaHR0cDovL3IxMS5pLmxlbmNyLm9y Zy8wKQYDVR0RBCIwIIIMb3RoZXJob21lLmNhghB3d3cub3RoZXJob21lLmNhMBMG A1UdIAQMMAowCAYGZ4EMAQIBMIIBAwYKKwYBBAHWeQIEAgSB9ASB8QDvAHYAPxdL T9ciR1iUHWUchL4NEu2QN38fhWrrwb8ohez4ZG4AAAGSQvDDVgAABAMARzBFAiEA 4mux6bwlRhkod0w2lpnEDzptWExR/w/edW/E5KqdHxsCIE+eSuU0VZ0BJScxH/a1 XVjRbSXVv1mh7es6d8MAZQ0KAHUA7s3QZNXbGs7FXLedtM0TojKHRny87N7DUUhZ RnEftZsAAAGSQvDDYAAABAMARjBEAiBitznteh8jOf0ouYy+0zGgb2Ertk+sqZBv cakVejJdrQIgbDdaOcdeCL0CBAWtqlyTSlZ5WMuAag7CZz+Gd4+s4zgwDQYJKoZI hvcNAQELBQADggEBAFtg1wIruQmPeWYoLZsFu1AXci01qCMWkIsYnXydayz9zZkn 2T1BO3e6UJUK4N96hQx0zOjAAnNf9o7Ky87ZX/ttImFNKwuJyzy7cxvrtNC5NFn2 0bt6R6ui4fFSO4px2h/7W6WBTnpoILYGpAxbi/7U8lOC8wSrROw/YCiy33sCqiqk xi8GBQv7kod1lVTdG/f3X6EgHT4T+yXhP+KXMecoqXUl7j8Z+ELdqC1ogW1hDDNR 2usRzqAzxToavls5+zgeFosck9TqaehFLRSBgpZTlb824DjdXOaGg3+YOWtg/Ic5 gjdW9XlAYHsckwD0FErnr1EGEGWt/XFm2KMGHRM= -----END CERTIFICATE----- subject=CN = otherhome.ca issuer=C = US, O = Let's Encrypt, CN = R11 --- No client certificate CA names sent Peer signing digest: SHA256 Peer signature type: RSA-PSS Server Temp Key: X25519, 253 bits --- SSL handshake has read 3132 bytes and written 405 bytes Verification: OK --- New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384 Server public key is 2048 bit Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE No ALPN negotiated Early data was not sent Verify return code: 0 (ok) --- --- Post-Handshake New Session Ticket arrived: SSL-Session: Protocol : TLSv1.3 Cipher : TLS_AES_256_GCM_SHA384 Session-ID: 0BAEE2E2596998FC051D88FA1D1A25EC671CC10D574E024DDE532762AF16A452 Session-ID-ctx: Resumption PSK: 5D8F0A9B82234EE41941D62904135FD72E4CBE4B7F0A8840504ACF7AFD1C452BDEBFB92FC5C3516C5E7582644D470DD5 PSK identity: None PSK identity hint: None SRP username: None TLS session ticket lifetime hint: 86400 (seconds) TLS session ticket: 0000 - c7 21 33 b9 cb a3 fb 39-3f 07 98 90 16 a1 dd 8f .!3....9?....... 0010 - ed bd 1a 29 fb dc 9e 46-56 ee 48 f8 f7 b6 24 00 ...)...FV.H...$. Start Time: 1728584237 Timeout : 7200 (sec) Verify return code: 0 (ok) Extended master secret: no Max Early Data: 0 --- read R BLOCK --- Post-Handshake New Session Ticket arrived: SSL-Session: Protocol : TLSv1.3 Cipher : TLS_AES_256_GCM_SHA384 Session-ID: 983BC3E889B11EFEB5782F6868276B49BBD14DF3B2C34EE453DCB79D0CBBC687 Session-ID-ctx: Resumption PSK: 0863E2FBD0E12E927F148560BC426747A03996188C8E0FE3F03AD6C7F8722BD53346145A27630C3B981CC58010B860EB PSK identity: None PSK identity hint: None SRP username: None TLS session ticket lifetime hint: 86400 (seconds) TLS session ticket: 0000 - 91 78 a8 cc 5e a5 a5 fd-f4 44 d2 cb ed 75 d1 05 .x..^....D...u.. 0010 - 7c 8b f3 1a 38 78 a1 25-94 e0 1a a9 27 3d 47 cd |...8x.%....'=G. Start Time: 1728584237 Timeout : 7200 (sec) Verify return code: 0 (ok) Extended master secret: no Max Early Data: 0 --- read R BLOCK closedThis certificate is owned by bolded textsubject=CN = otherhome.ca
-
@FrankM See, that's where I don't see what you're seeing. When I run the same command, the certificate chain looks fine:
$ openssl s_client -connect packages.nodebb.org:443 CONNECTED(00000003) depth=2 C = US, O = Internet Security Research Group, CN = ISRG Root X1 verify return:1 depth=1 C = US, O = Let's Encrypt, CN = R11 verify return:1 depth=0 CN = packages.nodebb.org verify return:1 --- Certificate chain 0 s:CN = packages.nodebb.org i:C = US, O = Let's Encrypt, CN = R11 a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256 v:NotBefore: Sep 18 09:05:41 2024 GMT; NotAfter: Dec 17 09:05:40 2024 GMT 1 s:C = US, O = Let's Encrypt, CN = R11 i:C = US, O = Internet Security Research Group, CN = ISRG Root X1 a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256 v:NotBefore: Mar 13 00:00:00 2024 GMT; NotAfter: Mar 12 23:59:59 2027 GMT ---
Copyright © 2025 NodeBB | Contributors