[nodebb-plugin-2factor] Two-Factor Authentication
-
In addition to regular authentication via username/password or SSO, a second layer of security can be configured, permitting access only if a time-based one-time password is supplied, typically generated/stored on a mobile device.
The Two-Factor Authentication plugin will expose this feature to end-users, allowing them to configure their
devices and enabling this enhanced security on their account.Requirements
- Requires NodeBB v0.7.2 or newer.
Installation
Install the plugin via the ACP/Plugins page.
Screenshots
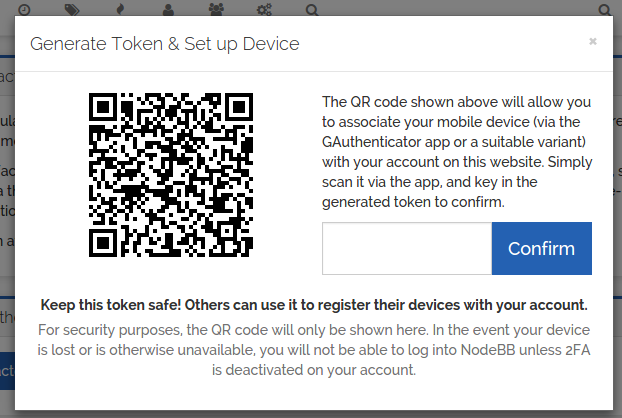
Token Generation Step
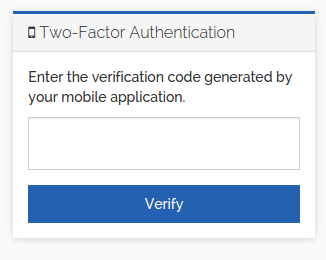
Challenge Step
Changelog
v1.0.2
- Added the ability to disassociate user tokens via the ACP page (in case users get locked out)
v1.0.3
- Bug: Fixed the browser title on the TFA settings page
- Bug: Fixed issue where hitting enter while keying in the validation code would abort the process
-
@julian I recently had my phone smashed by a drunk friend (I could just make out the numbers on a flickering screen) and discovered how terrible the "reset code" or "add code to another device" situation is with a new phone on sooo many websites where I had 2FA, even if you can get in with your current one.
-
Are backup codes supported now btw? I see a closed GitHub issue for them, which suggests they are.
-
@LB Yep, they are, although they are generated only when you start the 2FA setup process, so you will want to disable 2FA, trash your record, and re-generate one. The backup codes will be displayed a single time for you to record.
-
When I scan this with Authy or Google Authenticator it says "QR code is invalid" no matter how many times I create a new one. Is there a fix?
-
@cookieman768 The same situation(((
-
@julian The problem was solved with FreeOTP Authenticator (Android).
-
@ilya This plugin no longer works with 1.17. Error below
2021-04-23T13:18:12.371Z [4567/469428] - error: uncaughtException: Failed to lookup view "admin/dashboard" in views directory "/home/phenomlab/nodebb/build/public/templates" Error: Failed to lookup view "admin/dashboard" in views directory "/home/phenomlab/nodebb/build/public/templates" at Function.render (/home/phenomlab/nodebb/node_modules/express/lib/application.js:580:17) at ServerResponse.render (/home/phenomlab/nodebb/node_modules/express/lib/response.js:1012:7) at /home/phenomlab/nodebb/src/middleware/render.js:89:11 at new Promise (<anonymous>) at renderContent (/home/phenomlab/nodebb/src/middleware/render.js:88:10) at ServerResponse.renderOverride [as render] (/home/phenomlab/nodebb/src/middleware/render.js:64:14) at processTicksAndRejections (node:internal/process/task_queues:96:5) {"error":{"view":{"defaultEngine":"tpl","ext":".tpl","name":"admin/dashboard","root":"/home/phenomlab/nodebb/build/public/templates"}},"stack":"Error: Failed to lookup view \"admin/dashboard\" in views directory \"/home/phenomlab/nodebb/build/public/templates\"\n at Function.render (/home/phenomlab/nodebb/node_modules/express/lib/application.js:580:17)\n at ServerResponse.render (/home/phenomlab/nodebb/node_modules/express/lib/response.js:1012:7)\n at /home/phenomlab/nodebb/src/middleware/render.js:89:11\n at new Promise (<anonymous>)\n at renderContent (/home/phenomlab/nodebb/src/middleware/render.js:88:10)\n at ServerResponse.renderOverride [as render] (/home/phenomlab/nodebb/src/middleware/render.js:64:14)\n at processTicksAndRejections (node:internal/process/task_queues:96:5)","exception":true,"date":"Fri Apr 23 2021 14:18:12 GMT+0100 (British Summer Time)","process":{"pid":469428,"uid":1000,"gid":1000,"cwd":"/home/phenomlab/nodebb","execPath":"/usr/bin/node","version":"v16.0.0","argv":["/usr/bin/node","/home/phenomlab/nodebb/app.js"],"memoryUsage":{"rss":294481920,"heapTotal":195198976,"heapUsed":164432120,"external":74292726,"arrayBuffers":70953438}},"os":{"loadavg":[1.23,1.17,0.8],"uptime":340350.31},"trace":[{"column":17,"file":"/home/phenomlab/nodebb/node_modules/express/lib/application.js","function":"Function.render","line":580,"method":"render","native":false},{"column":7,"file":"/home/phenomlab/nodebb/node_modules/express/lib/response.js","function":"ServerResponse.render","line":1012,"method":"render","native":false},{"column":11,"file":"/home/phenomlab/nodebb/src/middleware/render.js","function":null,"line":89,"method":null,"native":false},{"column":null,"file":null,"function":"new Promise","line":null,"method":null,"native":false},{"column":10,"file":"/home/phenomlab/nodebb/src/middleware/render.js","function":"renderContent","line":88,"method":null,"native":false},{"column":14,"file":"/home/phenomlab/nodebb/src/middleware/render.js","function":"ServerResponse.renderOverride [as render]","line":64,"method":"renderOverride [as render]","native":false},{"column":5,"file":"node:internal/process/task_queues","function":"processTicksAndRejections","line":96,"method":null,"native":false}]} 2021-04-23T13:18:12.371Z [4567/469428] - error: Error: Failed to lookup view "admin/dashboard" in views directory "/home/phenomlab/nodebb/build/public/templates" at Function.render (/home/phenomlab/nodebb/node_modules/express/lib/application.js:580:17) at ServerResponse.render (/home/phenomlab/nodebb/node_modules/express/lib/response.js:1012:7) at /home/phenomlab/nodebb/src/middleware/render.js:89:11 at new Promise (<anonymous>) at renderContent (/home/phenomlab/nodebb/src/middleware/render.js:88:10) at ServerResponse.renderOverride [as render] (/home/phenomlab/nodebb/src/middleware/render.js:64:14) at processTicksAndRejections (node:internal/process/task_queues:96:5) -
v5.0.0 of the 2factor authentication plugin has been published. It now allows for concurrent second factors, so you can have both a hardware key and an authenticator app in use at the same time.
When challenged, you can use either option to verify your identity.
-
v7.4.0 of this plugin now notifies you in the event that your account was accessed, but the second factor challenge was not passed.
This provides a much-needed notification for the user that their password has been compromised and is in need of changing.
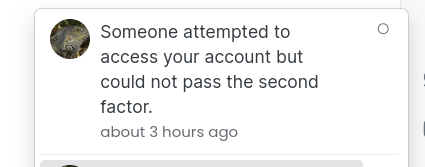
NodeBB (@[email protected])
Attached: 1 image The Two-Factor Authentication plugin that comes bundled with #NodeBB was just updated to v7.4.0. It now notifies you if your account was accessed, but the second factor challenge was not passed. If you see this notification, and it wasn't you, you just might want to change your now-compromised password! Oft forgotten, this feature provides much needed positive reinforcement that, yeah, #2FA works! #appsec #security #2factor
Fosstodon (fosstodon.org)
-
when i try to add a hardware key i instantly get the message "hardware key registration abborted" and in the logs i found this:
2023-11-20T06:03:39.301Z [4567/995] - info: [plugin/2factor] Denying socket access for uid 2 pending second factor.Any idea how I can fix this?







